Part III was posted here (and from there can be found the chain of links containing the full series of these posts—or search on “America’s Future” in my blog’s search functionality). In this final post of this occasional series, I’ll write about the general force structures needed to effect our Defense principles and policies. Much of what I suggest below will require technological development; however, none of that is futuristic—indeed, some of that technology already is in one or another prototyping stage today. Further, these force structures support another concept: never fight fair—only fight to win with maximum enemy casualties and maximum damage to enemy entity infrastructure and with minimum friendly casualties and minimum damage to friendly infrastructure. War is not a sporting event; national survival is in the balance.
I will write here about five essential forces: cyber, communications, space, “traditional,” and special operations. None of this is to deprecate other areas, for instance intelligence; this is simply a nod to practicalities: I’m writing a too-long post, not a book.
Guiding my remarks are two premises first articulated by former Secretary of Defense Donald Rumsfeld in his Known and Unknown: A Memoir. These are that the time required to recognize the nature of a new threat and to develop counters to it is far too long. Without going further into bureaucratic imperatives, the SecDef who’s going to bring about these force structures needs to have the courage and stubbornness, as well as the backing of his President and of Congress, to not waste time arguing with those who will not or cannot adapt to the new culture. Those roadblocks, civilian and military, need to be promptly and decisively terminated.
The other premise is that our systems, which include the people who use them as the critical part of each of those systems, must be more flexible and more lethal, while simultaneously being lighter and more mobile. This is especially critical for the individual soldier and Marine with his small arms, ammunition, communications, and battery load-out.
Our cyber forces, as I mentioned in an earlier post, must include both defensive and offensive capabilities. The easiest attack to mount is a simple, brute force denial of service, wherein the attacker simply overwhelms the targeted system(s) with requests for service. This can include such things as overloading the CPUs with computational demands or overloading the network interface card with demands for communications services. Other attacks include inserting malware into the computer system(s) for the purpose of corrupting data; blocking access to hard drives; and recording keystrokes (to collect passwords, for instance), collecting actual data, and then broadcasting the collected information back out of the compromised network to the attacker or an accomplice. Malware can be inserted through a variety of methods ranging from direct, hacked insertion to “social engineering,” where a user, while on his personal system outside the target network, is fooled into downloading malware onto a memory stick and then bringing that memory stick into the target network. This last is speculated to be one means by which the stuxnet worm was inserted into the Iranian networks.
Defensive forces here include physical and software firewalls and constant, proactive research into malware with associated development of counters to these. But they must also include human training—and not just the annual routine security refresher that’s so often used. Training in this area must be as active and rigorous as any of the rest of the soldier’s or Marine’s combat training—cyber combat is every bit as real and lethal. But another aspect of defense is to turn the attack and seize the initiative. Methods and software must be developed to trace malware—whether discovered in situ or during an insertion attempt—back to its source, with the tracing mechanism carrying its own malware for insertion into the originating network(s). The payload here should include both tracking/reporting software and software intended to disrupt/destroy the originating systems, with a capability of both automatic and manual remote triggering.
Offensive cyber forces will include force capabilities that look a lot like the active defense described just above, with the difference that the payloads here are being inserted on the attack, rather than in counterattack. The malware being inserted also will have a broader range of payloads: payloads designed for residence in computer chips manufactured for sale overseas, designed for specific systems in the enemy entity’s suite, and so on.
Our communications forces also will need both defensive and offensive capabilities. Communications always will be a prime target of our enemies, as they seek to isolate command from the forces in contact (for instance). Thus, communications systems must be protected from physical attack and electronic disruption. Brute force power-out on the transmission side will be useful as will be increasingly sensitive antennas on the receiving side. Both systems—and cyber systems generally—will need hardening against power surges, for instance from repeated EMP. Further, all communications must be encrypted using the strongest encryption possible consistent with rapid coding and decoding (which also puts a premium on communications-supported research into encryption techniques and CPU capacity and speed). Moreover, since none of this can be guaranteed 100% successful, the systems must be highly and rapidly redundant, and the codes—and code styles—rapidly changeable.
On the offensive side, enemy communications nodes of our choosing must be attacked and destroyed as early as possible in the conflict, with the replacement nodes also of our choosing just as promptly destroyed. I do not advocate blindly destroying all of his communications facility, however. Useful nodes should be identified, and these should be used for inserting misleading information into the enemy’s communications. Such insertions can range from falsified communications from his forces in the field (including individual terrorist cells or individual terrorists) providing misleading status to accessing an enemy’s display systems and placing false information onto them.
Notice here that there will be considerable overlap with other force structures. Destruction of communications nodes will involve either “traditional” or special operations forces, or both. Insertion of false information will involve (depending on the spoof being run) special operations forces and/or cyber forces. Cyber forces especially will be involved in hacking the enemy displays, and this will also require technological advances beyond today’s capabilities.
Our space force structure must be designed to give us both assured and rapid access to space, at all operational altitudes—including in the near term to lunar altitudes. Assured access includes more than lots of boosters sitting in the rack ready to be rolled out, though. Our launch facilities are woefully outdated, too few in number, and too slow to ready for a subsequent launch. Commercial launch facilities should be supported as well as government ones (and commercial access should be made available to the government ones on terms useful to both). This support, though, should not come in terms of “shared” costs, but more in terms of government getting out of the way of such things as licensing the facilities and each launch.
Military space facilities, both launch and on-orbit, need to be hardened against a variety of attacks: cyber, communications, energy weapon, and many forms of physical attack. Hardening against cyber and communications attacks have been described above. Energy weapon attacks can be defended in a variety of ways (while a variety of such attacks need technological advances in understanding their nature as well as means of defending against them): gas or dust ejections can attrit the arriving energy in a number of bandwidths. Reflective and ablative surfaces (with current technology, both capacities in the same surface aren’t possible; this is another area wanting research and advance) which can dissipate arriving energy before it penetrates beyond those surfaces are among those ways. Physical attack defenses include weapons that destroy incoming weapons before impact or fusing (whether individual “anti-missile missiles,” sprays of “gravel” to increase the likelihood intercept), evasive maneuvers by the targeted system (of greater or lesser utility depending on the mass and momentum of the target and the presence or absence of terminal guidance and maneuverability of the attacking weapon).
As above, there must be an offensive capability here, as well. Enemy space systems, including his on-orbit facilities, must be subject to destruction by our forces. I’ve suggested some attack mechanisms above. Our forces, though, must be capable of terminal maneuvering so as to defeat target maneuvers; they must be capable of penetrating a gravel shield (initially by overwhelming it with numbers of attacks from a variety of directions, rather than by paying the payload penalty from hardening each weapon against “gravel” impact—of dubious practicality, anyway, given the energies involved in the impacts); they must have energy of sufficient density, and with aiming quality sufficient to allow dwelling on the initial impact point long enough, to penetrate defenses.
This offensive capability also must integrate with special operations forces and “traditional” forces. While ballistic payloads of sufficient size can be deorbited to fall from orbit, survive reentry, and kinetically impact enemy launch facilities, communications nodes, and other targets (essentially, dropping high-speed rocks on them), attack by special operations and/or “traditional” forces will play a crucial role, as well. Moreover, offensive forces must be capable of destroying the enemy’s access to space at any time post-launch, as well: from boost to any staging section of flight, through cruise to pre-impact or pre-arrival at his own space facilities.
In my next post, I’ll complete the description of our needed force structures: a discussion of our “traditional” force structure and of our special operations force structure.
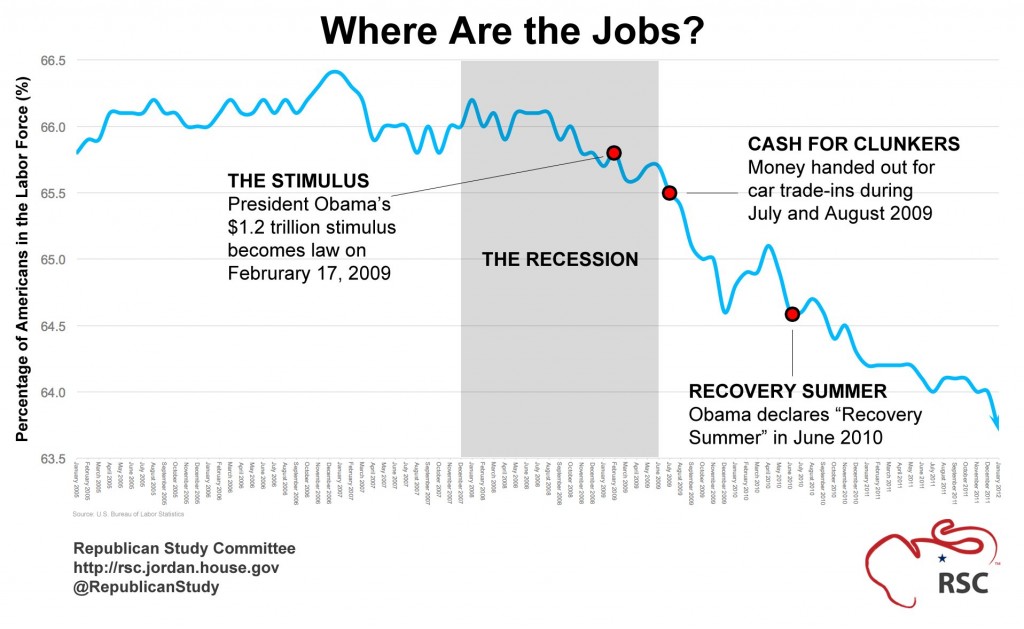 The RSC also points out that [emphasis theirs] 36.3% of working-age Americans do not have a job and are not even looking.
The RSC also points out that [emphasis theirs] 36.3% of working-age Americans do not have a job and are not even looking.