The subheadline of a Wall Street Journal article on cell phone security vulnerabilities presents the subject of my post.
The passcode that unlocks your phone can give thieves access to your money and data; “it’s like a treasure box”
The article then laid out the problem:
The thieves are exploiting a simple vulnerability in the software design of over one billion iPhones active globally. It centers on the passcode, the short string of numbers that grants access to a device; and passwords, generally longer alphanumeric combinations that serve as the logins for different accounts.
With only the iPhone and its passcode, an interloper can within seconds change the password associated with the iPhone owner’s Apple ID. This would lock the victim out of their account, which includes anything stored in iCloud. The thief can also often loot the phone’s financial apps since the passcode can unlock access to all the device’s stored passwords.
“Once you get into the phone, it’s like a treasure box,” said Alex Argiro, who investigated a high-profile theft ring as a New York Police Department detective before retiring last fall.
This image lays out the technique: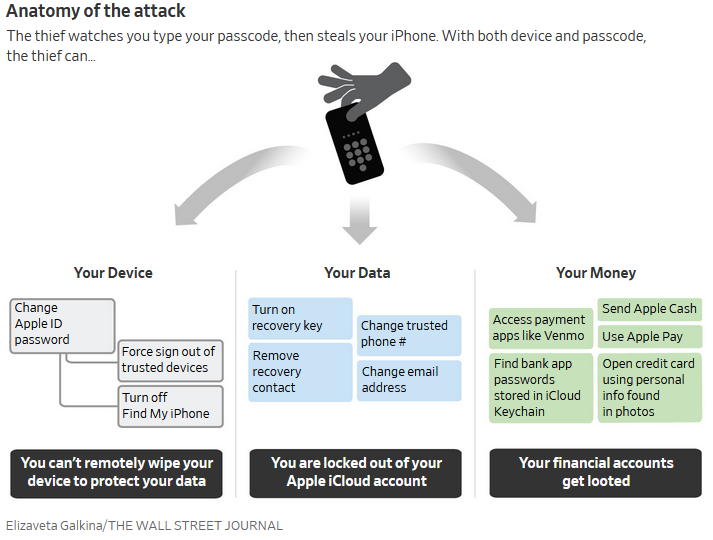 There’s nothing magic about iPhones in this regard, though; Android cell phones are just as vulnerable to this sort of attack.
There’s nothing magic about iPhones in this regard, though; Android cell phones are just as vulnerable to this sort of attack.
However, there are a couple of solutions to this, regardless of the type of cell phone you use. Each solution also works even better when done in concert with the other, and they rely on something old-fashioned: caution and concern for personal privacy.
One solution is to not use your cell phone to conduct any activity, not only financial, that you don’t want exposed to the public, much less to a thief. That way, if your cell phone is stolen, there’s nothing in it beyond your contact list that can be hacked. The potential cost of doing non-telephone things on your cell phone is far greater than the short-term convenience gained.
The other solution is to not store anything in the cloud. Keep your private material private by keeping it entirely within your home’s network, and ideally even more restricted: keep that information solely on your PC’s or laptop’s hard drive, or better, on an external hard drive that connects only via USB—and keep that external storage device separate from your PC/laptop.
Related, and subsidiary to all of that, don’t store passcodes or passwords on your PC/laptop, even via a passcode/word manager. In the unlikely event your laptop is stolen, or your PC is stolen via home break-in, that manager can be hacked at the thief’s leisure.
